Appearance
Workspace Settings
This section allows you to configure workspace settings specifically for this project. Define project-level security policies for data handling and access, and establish network policies to control workspace traffic within the context of this project.
Security Settings
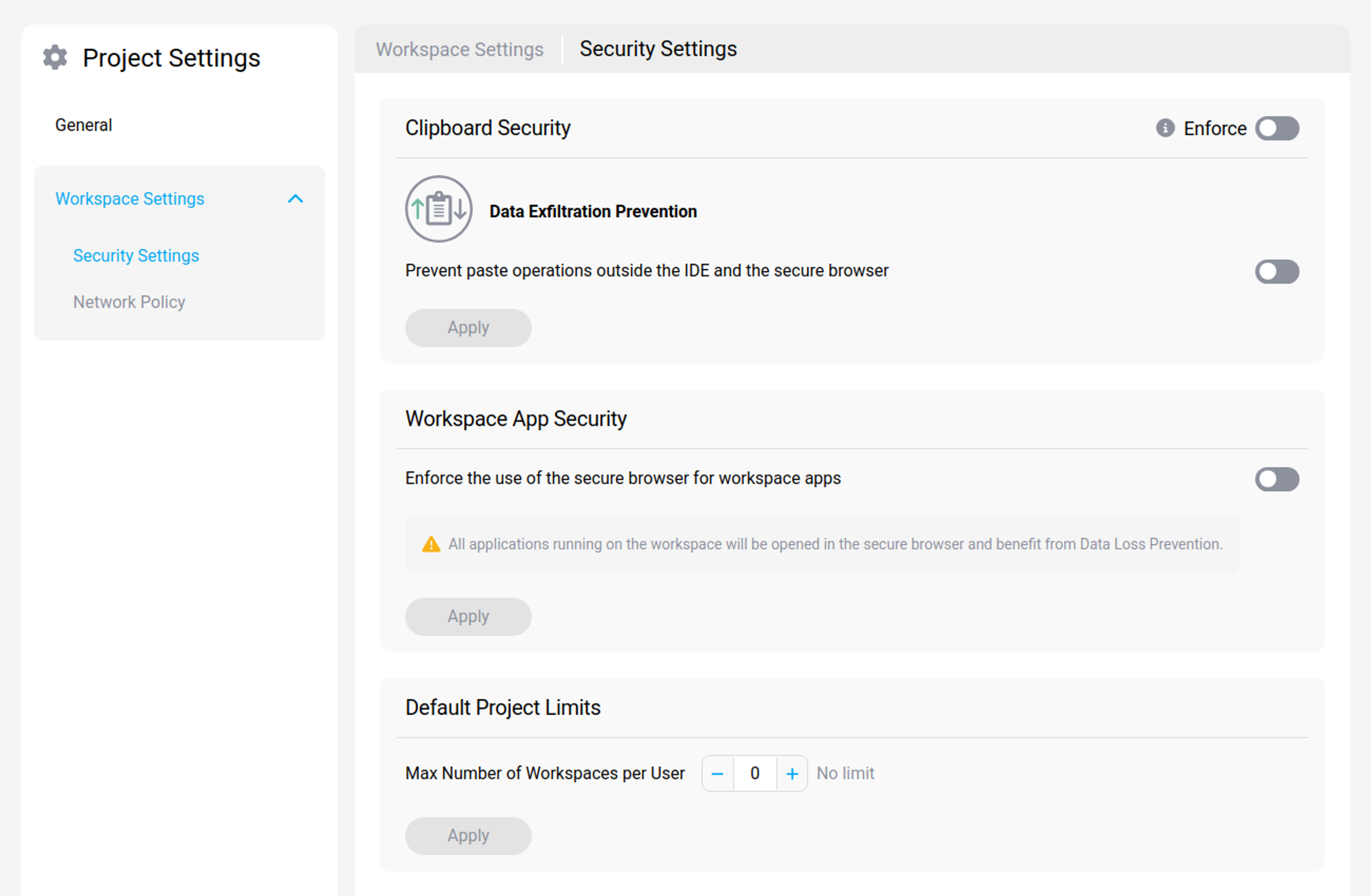
In the "Workspace Settings" section, the "Security Settings" enable you to implement multiple policies including Clipboard Monitoring, Workspace App Security, and Default Project Limits. These policies can be enforced to establish a foundational level of security across all workspaces within your project.
 Security Settings Section
Security Settings Section
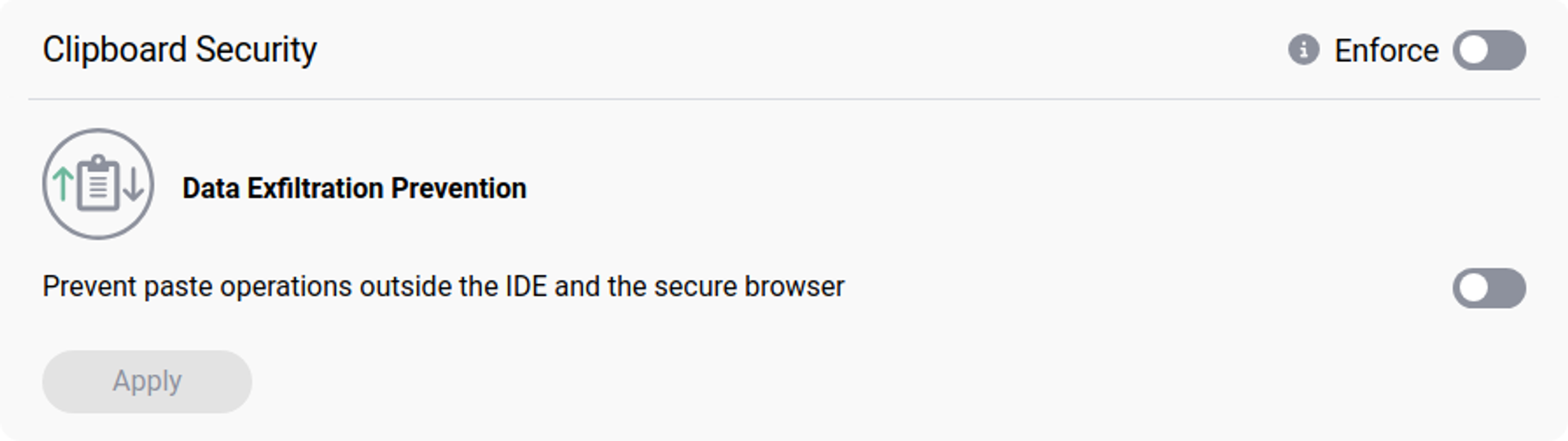
Clipboard Security
Clipboard Security implements Data Loss Prevention policies to safeguard against data leaks by disabling the ability to paste content from the IDE and secure browser into external applications.
 Clipboard Security Section
Clipboard Security Section
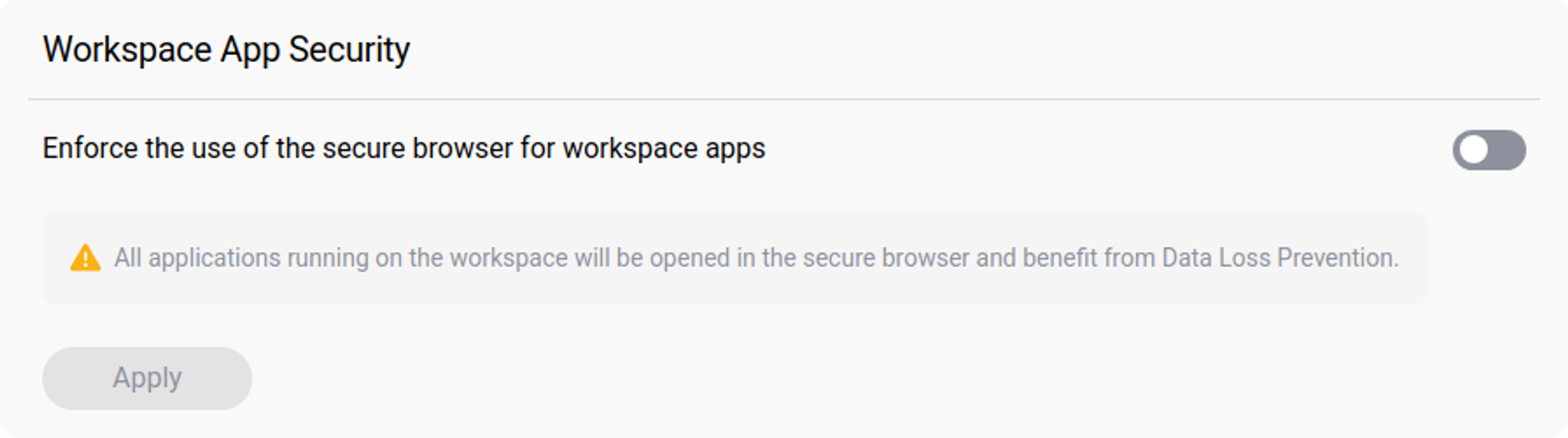
Workspace App Security
Workspace App Security allows you to mandate the use of a secure browser for workspace applications, ensuring that developers can share the applications they are developing in a protected environment. When used in conjunction with the Clipboard Security policy, this feature helps to prevent any potential data exfiltration from workspace applications.
 Workspace App Security Section
Workspace App Security Section
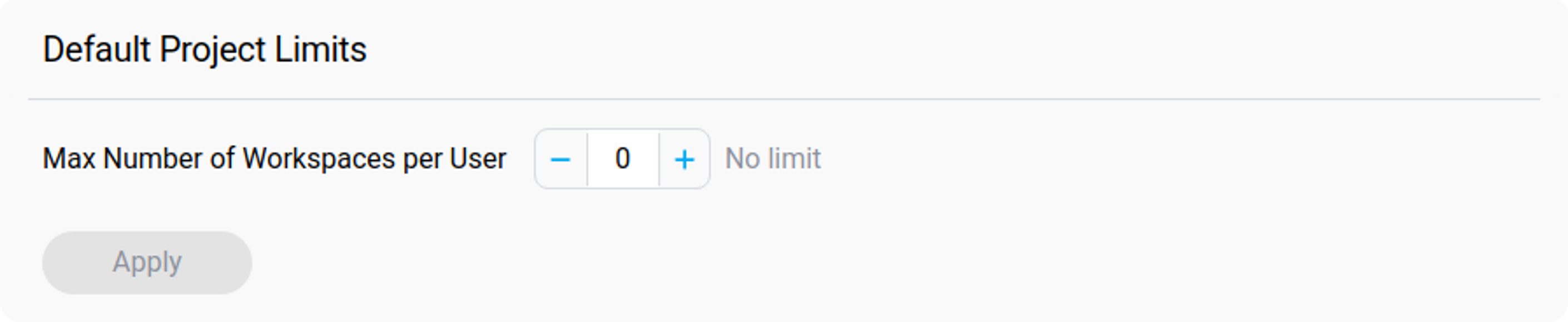
Default Project Limits
Default Project Limits can be set to cap the number of workspaces a user can create. This not only aids in resource monitoring and reduces unnecessary workspace proliferation but also contributes to cost efficiency by avoiding the operation of unused workspaces.
 Default Project Limits Section
Default Project Limits Section
Enable Remote Development Over SSH
Remote Development Over SSH gives you the option to permit or deny developers the ability to connect to their workspaces via SSH. While convenient for certain tasks, this feature must be used judiciously as it can reduce the effectiveness of local IDE data loss prevention measures.
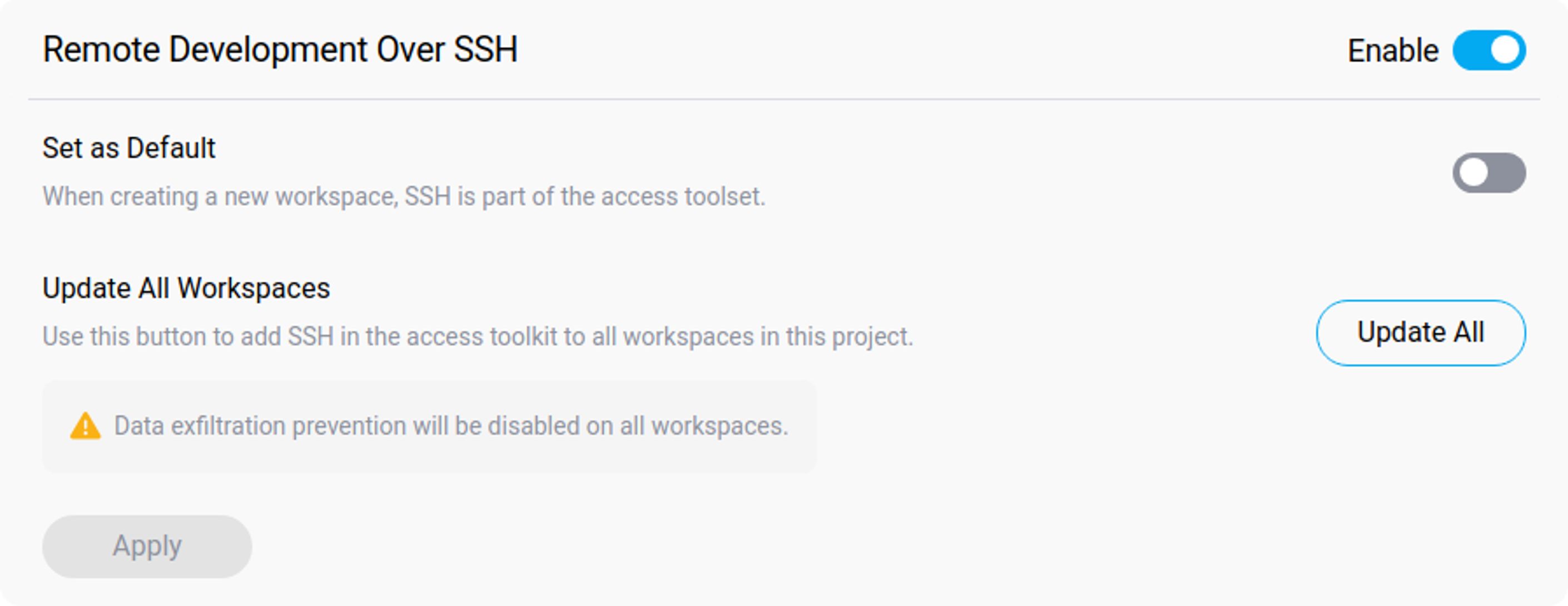 Remote Development Over SSH Section
Remote Development Over SSH Section
Network Policy
Network policies are attached to workspace and enable fine-grained network traffic control. Network traffic is identified using combinations of IP addresses, port and domain names. Once a network policy is attached to a workspace, all outbound traffic is enforced by the rules in the policy and the workspace's user cannot circumvent the restrictions.
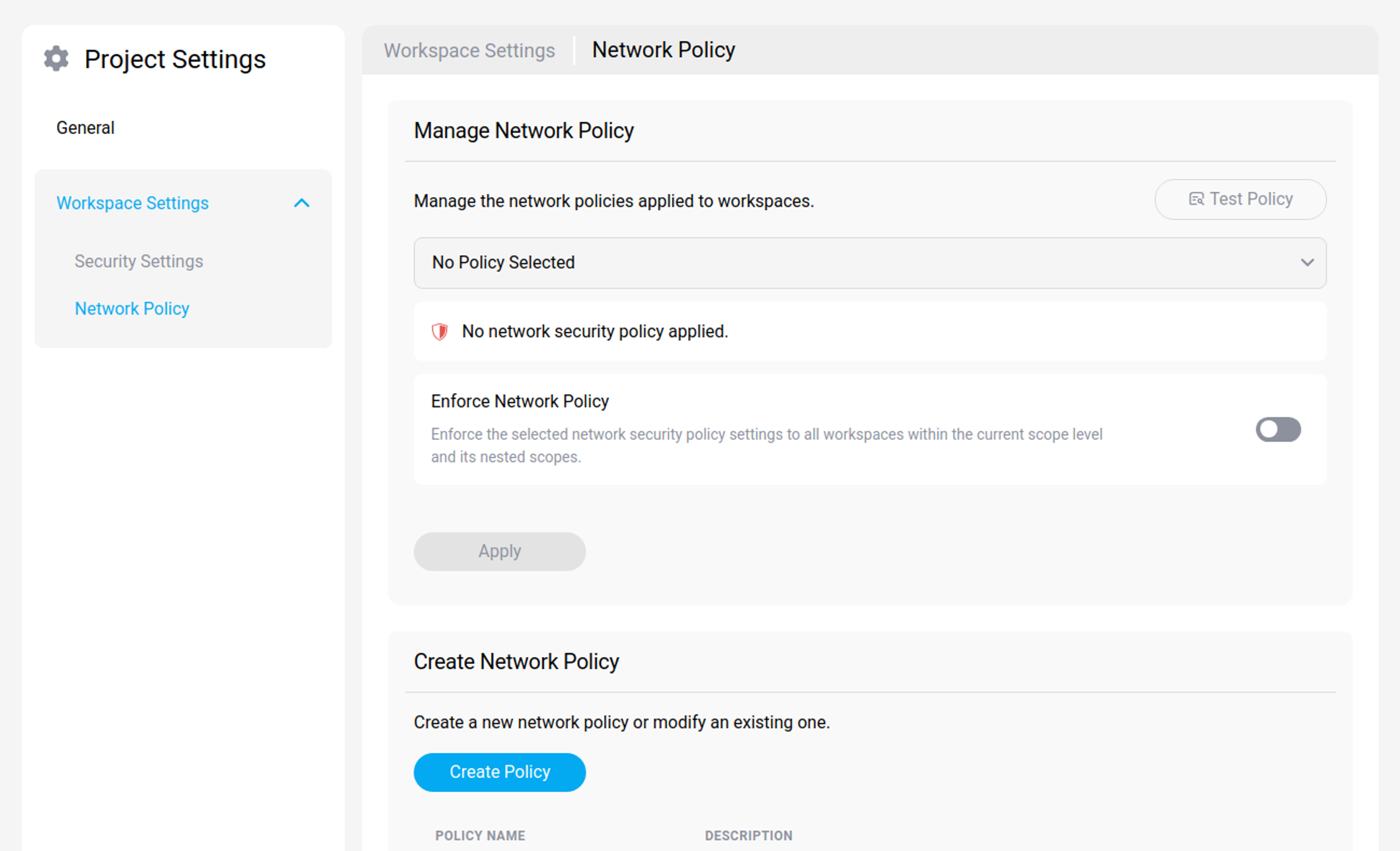 Network Policy Settings Section
Network Policy Settings Section
Default Network Policies
Three default policies are available in a project. An administrator can create a new Network Policy if needed.
| Name | Scope | Description |
|---|---|---|
| Monitor Traffic | Project | This is a standard policy to monitor the outgoing traffic to the workspace. It will cause the generation of log events in the Audit dashboard. |
| Restrict Traffic | Project | This is a standard policy to restrict outgoing traffic from the workspace. It will block all traffic except to attached repositories and domains. Failed network requests are shown in the log events in the Audit dashboard. |
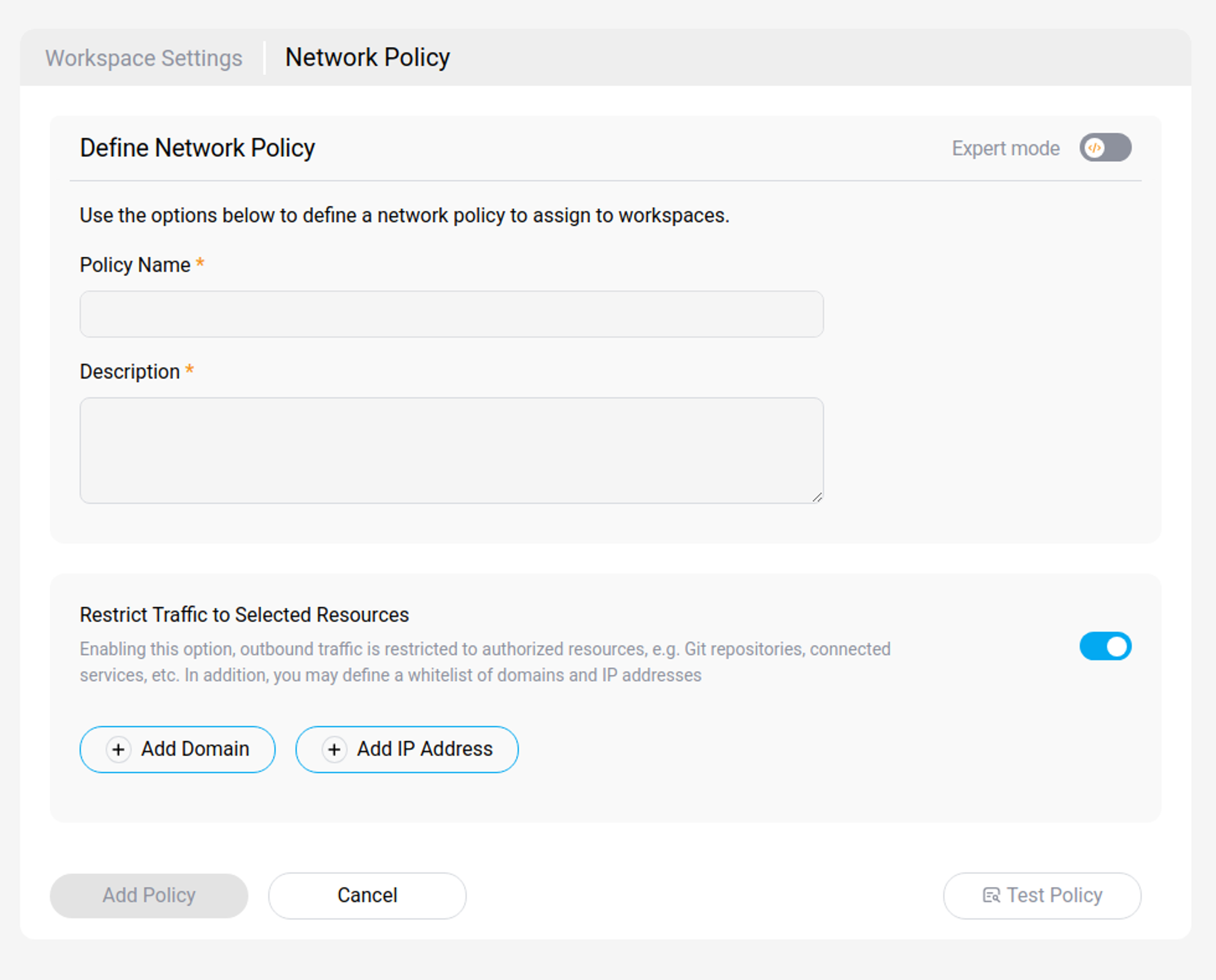
Add a Network Policy
You can create a Network Policy by pressing the "Create Policy" button.
 Add Network Policies Section
Add Network Policies Section
You will need to enter the following information:
- Name, a name to identify the policy,
- Description,
WARNING
Be careful when naming and describing a new policy. A misleading name can end up in giving too many permissions to a user.
- Log and record outbound network traffic (default),
- Restrict Traffic to Selected Resources (optional), All traffic will be restricted, expect for end systems added to your whitelist
- Add each application that you want to whitelist
- Add Domains that you want to whitelist, and indicate whether to include subdomains
- Add IPs that you want to whitelist
Edit or Delete a Network Policy
You can edit or delete a Network Policy by clicking on the "..." icon next to its class level.
